Why is Two-Factor Authentication (2FA) Important for Remote Access?
- Written by: Dave Nelson
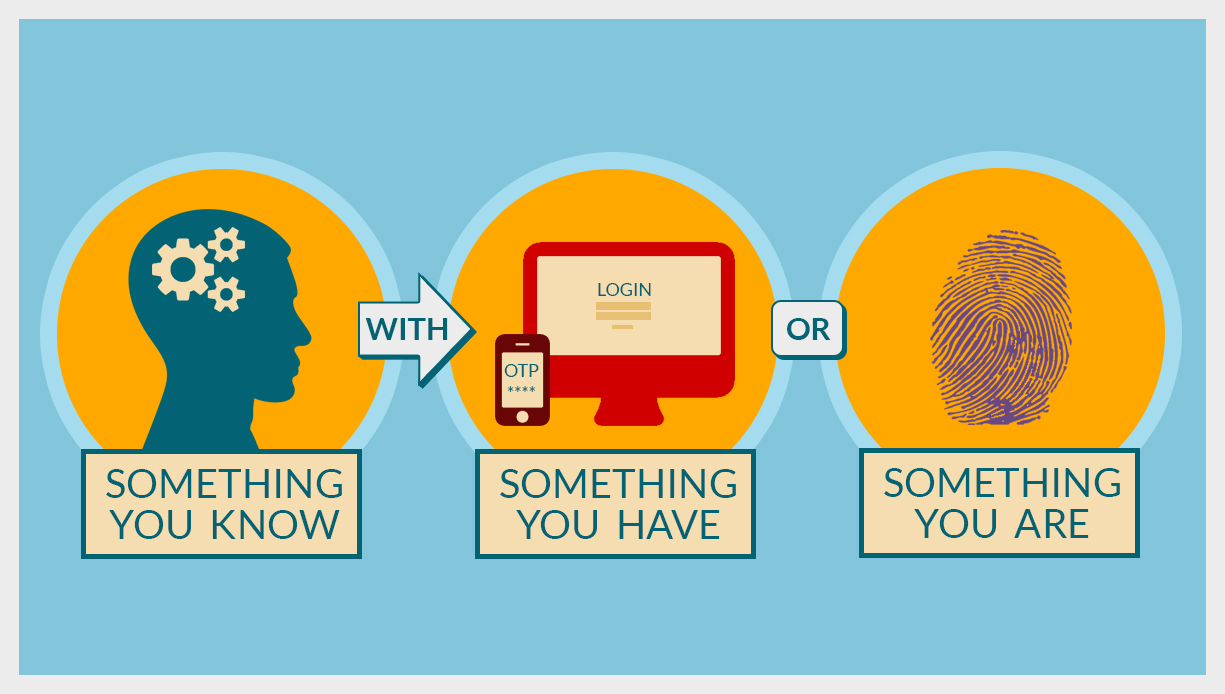
Two-factor authentication (2FA) is often a hotly debated security control. The argument for two-factor authentication from an information security perspective is that it helps ensure that only the actual user who is authorized to use the account is logging in. By using something you know like a password, with something you have like a one-time token or something you are like a fingerprint, you can add to the assurance that the person using the account is actually the authorized individual. On the negative side, many would say the cumbersome initial enrollment and subsequent login process has too much of an impact on usability.
Asking the Right Questions
Many organizations battle these questions when considering the need for 2FA. We always guide our clients in making risk based decisions. Which systems or applications are at the highest risk for unauthorized access attempts? What is the impact of an unauthorized user getting access to the system? When you start from this perspective it helps guide the cost and implementation discussions.
What options are available for implementing 2FA? A common method is to use SMS, or text messages, to send a unique code to a user’s phone. This eliminates the old “key fob” or “pin cards” from decades past. This ensures a user is authorized.
What about when you want to make sure only authorized computers are used to gain remote access? You can use a digital certificate or 802.1x protocols to quarantine the system until it has been interrogated and approved.
Making Your Decision
The reality is that remote access systems, including web based systems, are under unprecedented attack. The attacks are getting more persistent and more complicated. To keep up, the status quo has to change. Two-factor authentication, for remote system administration by IT staff or vendors, must be used in today’s world. The risk is just too great. After that, it’s really a business decision. One that requires more than just the IT team’s input. Have the discussion with your business unit, risk management, IT and customer service teams to determine if two factor authentication is the right approach. And remember, there are multiple approaches to 2FA, make sure you’re using the right one to get the outcomes you desire.






