Your 2025 CISO Roadmap
- Reading Time: 5 mins
A secure organization doesn’t happen by chance—it’s built with intention, focus, and a proactive plan. As cyber threats continue to grow and evolve, so must your defenses. Regularly revisiting and refining your cybersecurity strategy ensures your organization stays resilient and compliant in the face of emerging challenges.
The most effective approach? A clear and actionable roadmap to help guide your security efforts throughout the year. Below, we outline a cadence-driven roadmap for 2025, packed with best practices and tips to help CISOs and IT managers focus on the essentials while staying agile for the unexpected.
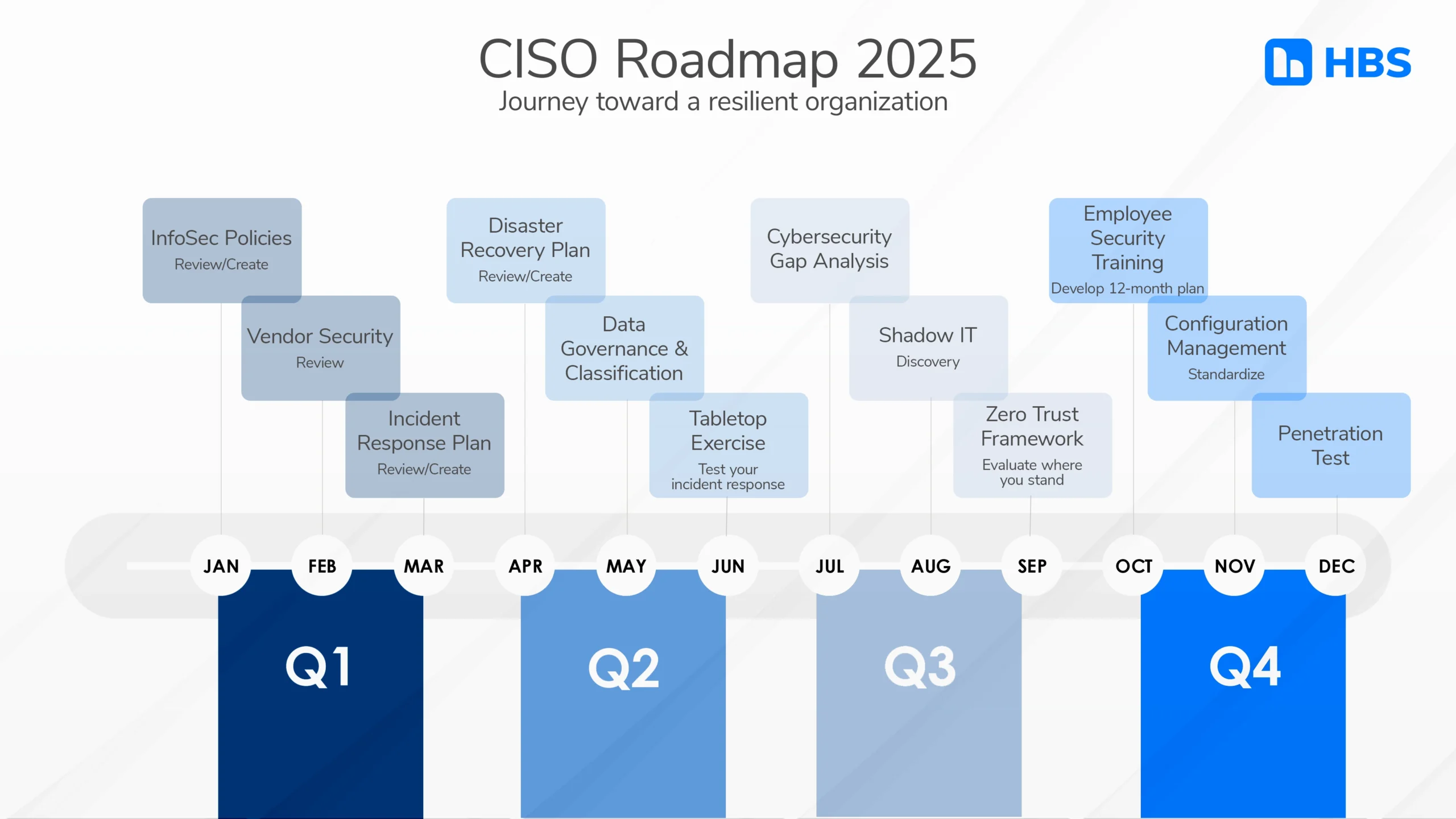
Quarterly Focus: Simplify and Strengthen Security
We’ve found that breaking cybersecurity milestones into quarterly goals creates a steady, manageable path to security maturity. Don’t get caught up in these quarterly suggestions as a rigid timeline—this is about having a plan and sticking to it.
In our example below, we’ve included three initiatives per quarter, but these can and should be altered to align with your team’s capacity and priorities. What matters most is consistent progress toward stronger security.
Quarter 1: Lay the Groundwork
- Review Policies: Begin the year with a comprehensive review of your information security policies. Update them to address emerging threats like AI-powered phishing, new regulations, and technologies like generative AI, and identify any new policies that need to be created—like an AI policy.
Pro Tip: Use this baseline checklist so no critical areas are overlooked.
- Vendor Security Checks: Evaluate third-party vendors for security risks. Cybercriminals often exploit weak links in supply chains. Conduct security questionnaires and request evidence of compliance certifications.
- Incident Response Plan (IRP): Refine your IRP, and make sure everyone knows their roles during an incident. Don’t have one? Now’s the time to build it.
Quarter 2: Boost Preparedness
- Disaster Recovery Plan (DRP): Review your DRP to make sure it is up-to-date and has been tested in realistic scenarios. Address any gaps identified during testing.
- Data Governance: Review data retention policies and classify data based on sensitivity. Align these with regulatory requirements while minimizing unnecessary data storage.
Pro Tip: Proper data classification improves protection, compliance and incident response when breaches occur—so do the work now to make it easier when a disaster happens.
- Tabletop Exercises: Simulate incident scenarios to test your team’s readiness. Here is how you conduct an effective tabletop exercise, and here are some scenarios for Ransomware, Business Email Compromise, and System Compromise/Double-Extortion Ransomware.

Quarter 3: Strengthen Security Posture
- Cybersecurity Gap Analysis
A holistic evaluation of your current security posture against frameworks like NIST or CIS Controls will identify gaps, and help you align with organizational goals. - Shadow IT Discovery
Look into any unauthorized tools and applications being used within your organization—this increasingly includes Shadow AI.
Pro Tip: Employee surveys, network traffic monitoring, and EDR tools are some of the ways to identify Shadow IT.
- Zero Trust Framework Review
Evaluate where your organization stands on its Zero Trust journey. Zero Trust isn’t a product; it’s a strategy. Focus on areas like network segmentation, identity verification, and device trust.
Pro Tip: Map out quick wins, like tightening multi-factor authentication (MFA) and enhancing user identity controls.
Quarter 4: Finish Strong & Prepare for 2026
- Employee Security Training Program: Use this time to establish a regular cadence for cybersecurity awareness training for the next 12 months. Security training shouldn’t be a one-and-done effort—most experts (and we agree) recommend conducting it, at least, 2-3 times per year or every 4 to 6 months. Deliver engaging, role-specific training that emphasizes phishing recognition, secure password practices, and reporting suspicious activities.
Pro Tip: Partner with a security training expert to develop and keep your program relevant, impactful, and aligned with the latest threat trends. A partner like HBS can provide fresh content, interactive simulations, and expert insights to keep your team engaged and prepared year-round.
- Configuration Management: Standardize system configurations and eliminate outdated settings that could leave your organization exposed.
- Penetration Test: Conduct a penetration test to identify and address any remaining vulnerabilities before year-end. Pen tests simulate real-world attack scenarios, helping you uncover weaknesses in your systems, networks, or applications that might have been missed.
Pro Tip: Pair automated vulnerability scans with manual penetration testing for a deeper, more thorough assessment of your security posture. Use the results of both to prioritize fixes and strengthen defenses heading into the new year.

Your Always-On Checklist
In addition to quarterly priorities, maintain these ongoing practices to ensure a consistent security posture: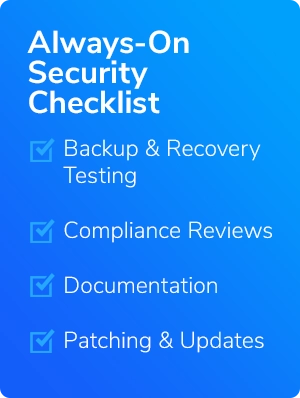
- Backup and Recovery Testing: Regularly verify backups and rehearse recovery processes.
- Compliance Reviews: Stay ahead of evolving regulations (e.g., PCI DSS, HIPAA) by conducting periodic compliance audits.
- Documentation: Keep complete and accurate records of everything—all audits, updates, training sessions, exercises, policies, etc.
- Patching and Updates: Don’t let outdated systems become easy targets. Prioritize patches for critical vulnerabilities, automate updates when possible, and monitor all systems to ensure no gaps. Regularly update operating systems, applications, firmware, and security tools to maintain resilience against emerging threats.
How to Stay Consistent
If you don’t have a cybersecurity strategy or roadmap, building them from scratch might seem a bit overwhelming. Here are some tips to get you started:
- Assign Ownership: Designate specific individuals or teams to own each task or goal. Clear accountability decreases the chances that nothing slips through the cracks.
- Leverage Automation: Use tools to automate routine tasks like patch management, compliance tracking, and network monitoring.
- Document Progress: Maintain a central log of actions, updates, and results for easy reference during audits or reviews.
- Engage Experts: Partner with external security experts for advanced assessments or managed services to ensure thoroughness and save time.
Build Resilience, One Step at a Time
By adopting a regular cadence of updates, reviews, and training, you’ll not only strengthen your defenses but also foster a security-first culture throughout your organization.
Cybersecurity is a journey—one you don’t have to navigate alone. Whether you’re building your roadmap or fine-tuning defenses, our experts are ready to help. Let’s make 2025 the year you move security from reactive to resilient.