Cybersecurity Trends: The Next Generation of Endpoint Protection
- Written by: Trevor Meers

One of this year’s biggest cybersecurity trends promises help for IT professionals drowning in messages pouring in from every corner of their technology stack. If that sounds familiar, it’s worth taking a few minutes to learn what Extended Detection and Response (XDR) solutions can do. These platforms recognize that gathering more data isn’t the solution. The real challenge is collecting the right data from every corner of your technology ecosystem and coordinating an effective response in real time.
XDR expands on the capabilities of traditional Security Information and Event Management (SIEM) and Endpoint Detection and Response (EDR) tools. While those resources undoubtedly made organizations more secure, they can leave a lot of gaps, especially in settings without dedicated security experts managing the tools. With all the diverse layers in most security stacks and the dramatic rise in employees working from home, it’s time for a leap forward. That has driven the development of XDR, which encompasses SIEM, next-generation endpoint protection and threat hunting.
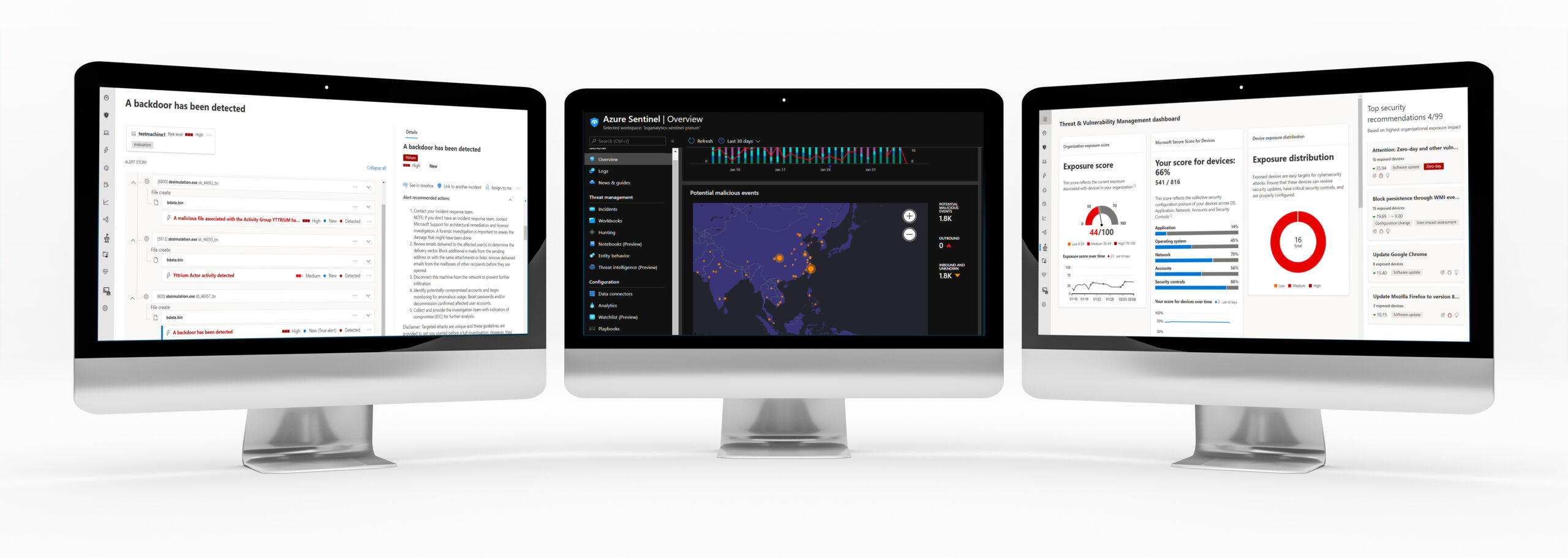
XDR solutions provide a more complete view of activities across your entire data estate and take proactive action against hackers. XDR can:
- Monitor and protect data across endpoints and core infrastructure
- Extend protection into the cloud
- Provide a single monitoring environment
- Consolidate log/event management
- Constantly incorporate cybersecurity best practices from incidents happening around the globe
XDR systems automate much of the monitoring and response, thanks to artificial intelligence and machine learning. With a cybersecurity consultant fine-tuning the system, XDR solutions continually spot emerging threats unique to your environment and stop them in their tracks. In this blog, we’ll summarize how XDR platforms work. And in the next post, we’ll share examples of how a well-tuned XDR system gets more effective every week thanks to customized provisioning, playbooks and more.
Why Your Security Stack Could Be Better
You’re probably wrestling with a security stack that consists of multiple tools for endpoint protection, SIEM, antivirus and more. Those tools most likely come from a variety of vendors and stretch across on-prem, cloud, and remote work environments. With alerts popping up each day on multiple dashboards, your security stack tends to feel less like a well-oiled defensive machine than a loose coalition of militias spread across your frontier. It’s hard to tell when two alerts coming from different corners of your environment are actually part of a single, larger event. All that distraction from false positives and alert fatigue leaves bad guys a lot of defensive gaps to sneak through and a lot of network chatter to hide in.
Larger cybersecurity trends only amplified the challenge in 2020 as most organizations saw their workforce scatter across a wide range of personal devices and unknown networks. In most organizations, it’s time for a solution that pulls all of it together.
How XDR Improves Endpoint Protection
XDR’s basic value proposition is monitoring the full extent of your technology ecosystem, turning daily noise into a meaningful signal and into actions that actively stop threats. In a simple example, XDR will notice a correlation between something happening on one of your firewalls, something happening on one of your endpoints and an activity in the cloud. Before XDR, those may have simply shown up as multiple alerts on multiple dashboards. XDR connects the dots and surfaces a meaningful alert. In one recent test, for example, Microsoft’s XDR solution used its machine learning tools to reduce 1,000 alerts down to 40 high-priority incidents. Default rules associated with traditional SIEM solutions typically don’t provide enough customization or sophistication to protect businesses like that. Several factors can cause this, but the problem usually involves too many alerts that turn into false positives and lead to alert fatigue.
An XDR solution offers not only advanced threat detection, but the ability to stop threats, even if it’s an attack no one has ever seen. With a traditional SIEM/SOC setup that lacks properly tuned automation rules, alerts travel to an incident responder, who must determine whether the activity represents a threat. If they decide it’s a bona fide security event, they then must identify the action to take and then manually deploy the proper remediation. In an XDR environment, all of that happens automatically, sometimes within milliseconds.
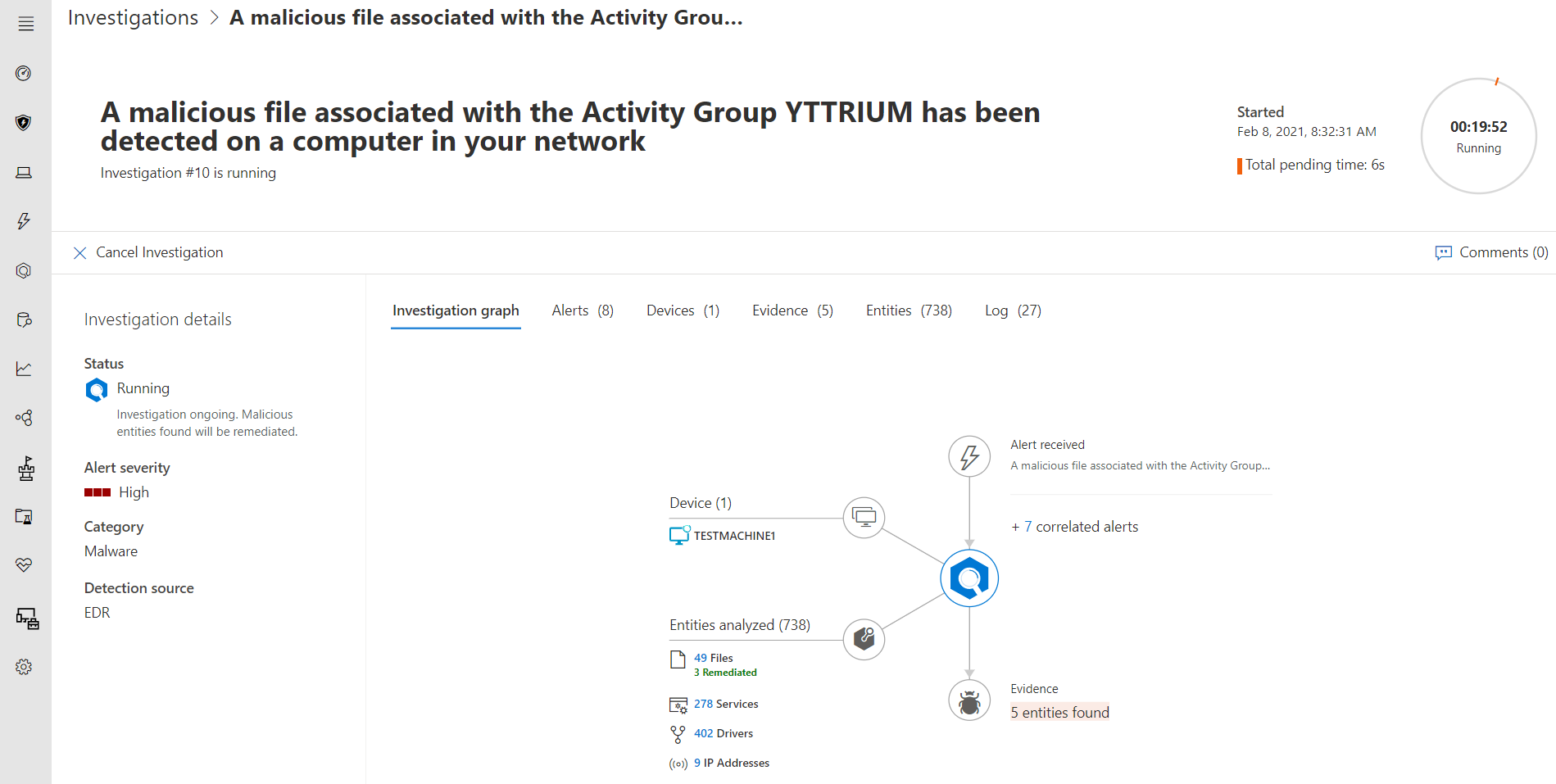
An XDR solution typically consists of the following elements:
- Endpoint detection and response (EDR)
- SIEM
- Security Orchestration, Automation and Response (SOAR) capabilities
- Threat-hunting capabilities
- Playbooks
- Human analysts (whether on-prem or contracted)
XDR actively monitors traditional devices such as servers, routers, firewalls, endpoints, mobile devices and IoT devices. But it also extends to cloud computing and storage services, as well as SaaS tools such as Microsoft 365, Dropbox and more.
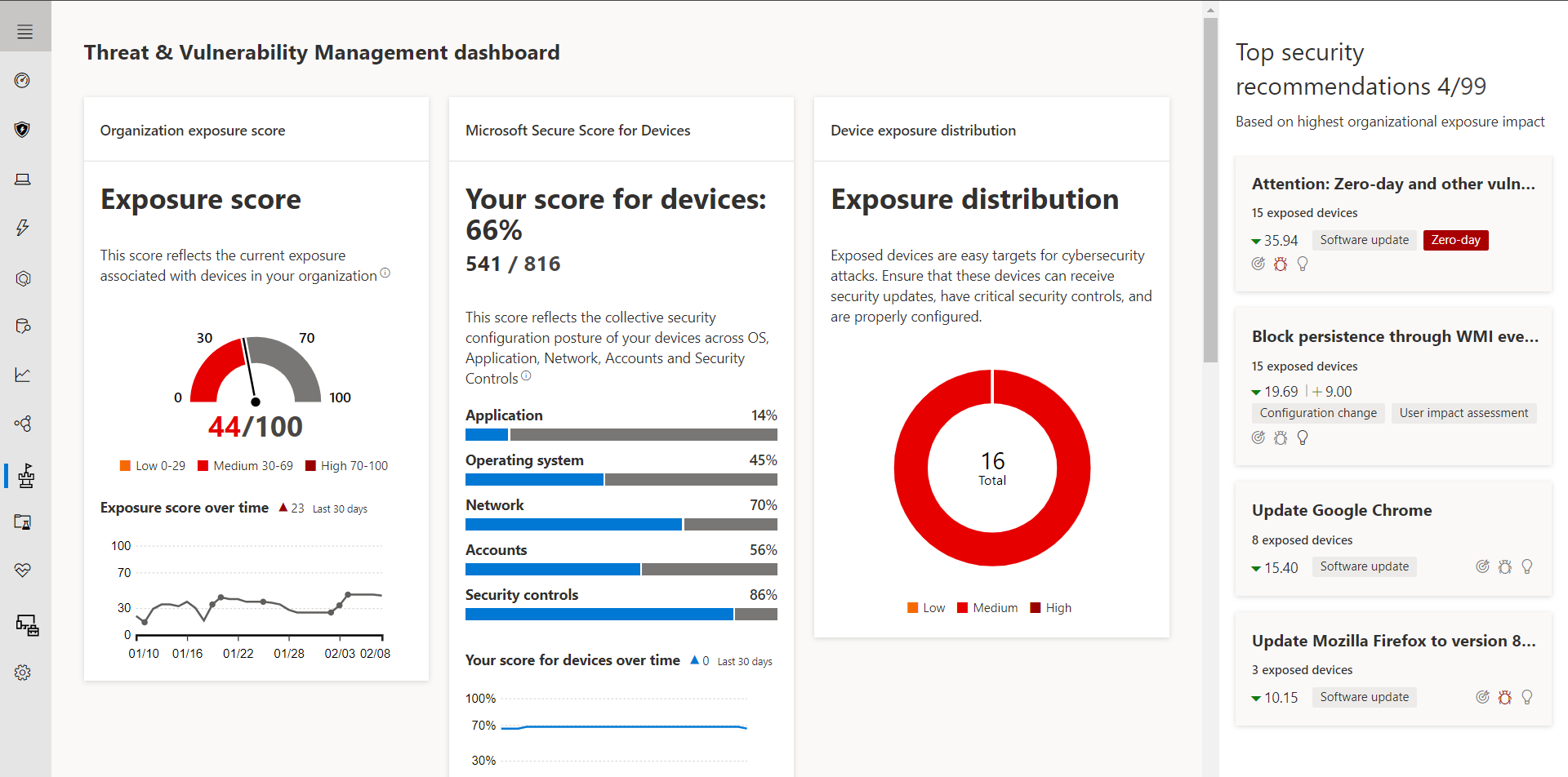
When you open the XDR dashboard, you’ll see how a threat entered your system, the damage it’s trying to do and how it’s attempting to pivot among different devices. And thanks to XDR’s threat hunting and response features, it can close off attack vectors long before you review the alert or report.
As you consider the best way to protect your organization in a cost-effective way, we recommend exploring the advantages of moving to Managed XDR.






