How Software Supply Chain Attacks Work
- Written by: Lucas Woodland

One of 2021’s biggest cybersecurity storylines has been the jump in supply chain attacks (they’ve jumped fourfold this year in some reports). These attacks turn the breach of a single organization into a massive headache for hundreds of partner companies. One of the most famous examples was the breach of Kaseya in July. That attack eventually enabled the REvil ransomware organization to encrypt the data of hundreds of companies worldwide as the attack cascaded outward from Kaseya to managed service providers (MSPs) to small/medium-size businesses. In a supply chain attack, the threat comes from one of your trusted software providers who hackers turn into a Trojan horse before anyone realizes what’s happening.
In this post, we’ll break down how supply chain attacks happen and what you can do to protect your system from these threats that arrive when your most trusted vendors unknowingly pass a big problem along to you.
Basics of Supply Chain Attacks
In what you might think of as a traditional hack, threat actors target one company and conduct reconnaissance to find vulnerabilities they can exploit. Then the threat actor breaks into that specific victim's computer network to exfiltrate data, launch ransomware, etc.
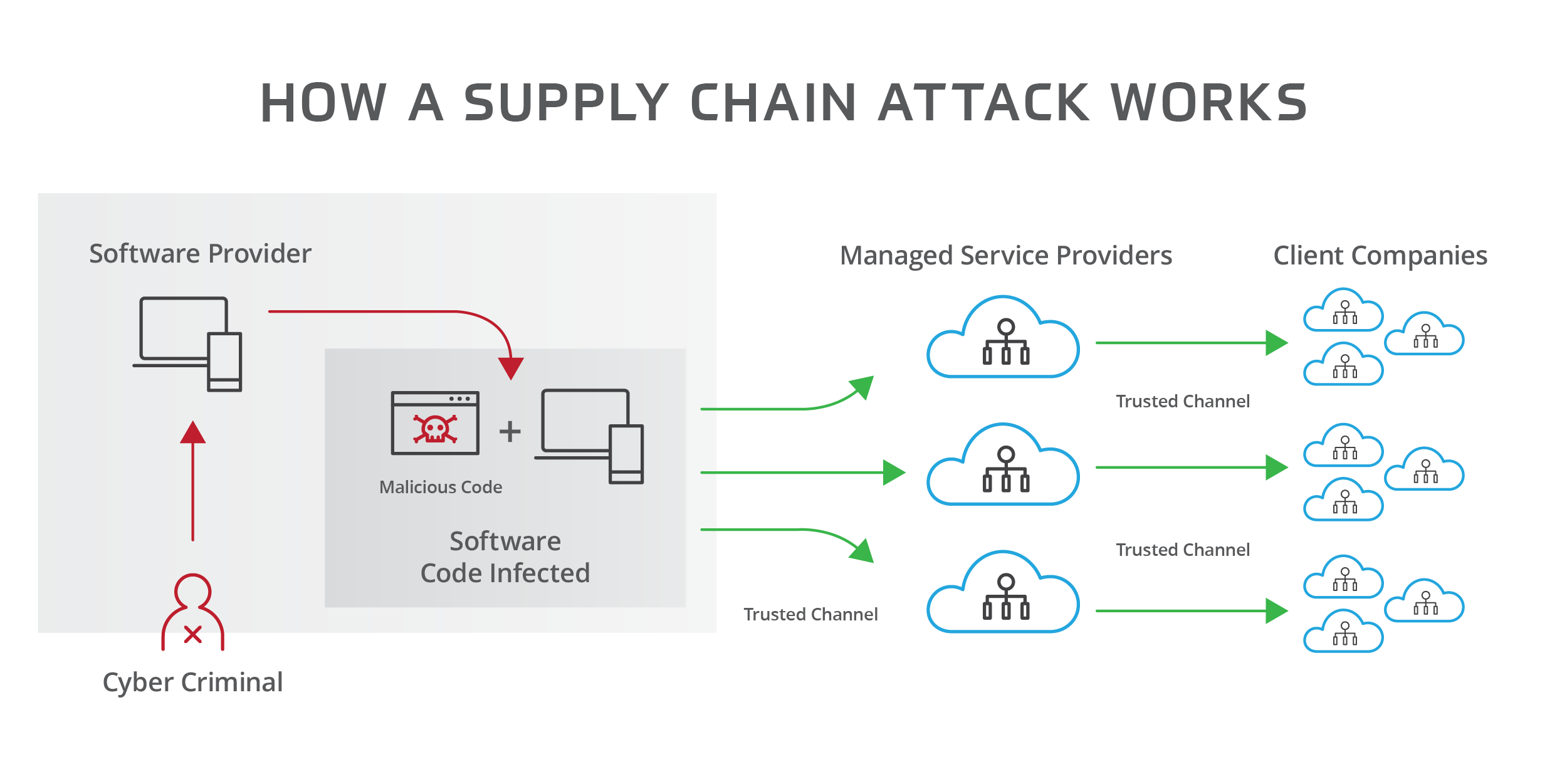
During a supply chain attack, the threat actors take the same initial steps, but their focus is upstream. They will compromise and infiltrate a trusted vendor that supplies software or IT services to many other companies. In this kind of attack, the goal isn’t focused on data exfiltration or launching ransomware on the vendors’ systems. Rather, hackers intend to sneak malware into the “supply chain” of software updates that the company installs on its customers’ computers. From a hacker’s perspective, these attacks are more efficient and have a greater impact because they leverage IT vendors that already have established and authorized connections into their customers’ network and systems. That means the malware can deploy across hundreds of companies and systems virtually undetected.
Every client of the IT vendor under attack becomes part of the attack. This blows up the “security by obscurity” belief that many smaller companies adopt. They think that because they’re small, they won’t be targeted by threat actors. But with supply chain attacks, tiny companies face just as much risk as big, high-profile enterprises.
The Kaseya Case Study
To understand these attacks, let’s break down the famous 2021 breach of Kaseya, an IT management software provider that mainly serves MSPs. On Friday, July 2, Kaseya’s incident response team identified a security incident related to Kaseya VSA. Their VSA (Virtual System Administrator) product delivers automated software patching, remote monitoring, and other capabilities so MSPs can seamlessly manage their customers' IT infrastructure. After breaking into Kaseya, the threat actors infected 50-60 MSPs. From there, they infected approximately 1,500 of the MSPs’ clients. The threat actors encrypted the victims’ data, effectively shutting down systems and networks. In Sweden, for example, the supermarket chain Coop closed 800 stores when its cash registers and payment processing systems went down—all because of a breach that was originally two steps removed from Coop’s systems.
The threat actors initially demanded $70 million to decrypt the systems, but later lowered the demand to $50 million. It appears that Kaseya refused to pay the ransom and received a decryptor tool from a third party on July 21 (yes, that’s nearly three weeks after the problem was discovered). With this tool, Kaseya was able to assist victims in restoring their systems and networks.
The SolarWinds Case Study
The SolarWinds breach that dominated headlines in December 2020 was another supply chain attack. Russian hackers, working for the Russian government, injected malicious code into SolarWinds’ IT management tool Orion, which gave the attackers access to thousands of systems when it was deployed. SolarWinds reported that up to 18,000 clients had installed the update with that malicious code. The victims of this attack included both private companies and government agencies, including NASA, the State Department, the Department of Defense, and the Department of Justice. The hackers didn’t demand a ransom, which indicates that this attack focused on espionage.
Why Supply Chain Attacks Are Increasing
Supply chain attacks are hard to defend against because they use software updates from trusted vendors. Organizations have always been concerned about infections that come from employees opening phishing e-mails with malicious attachments; clicking links and revealing their login credentials; or plugging a virus-infected USB drive into their computer. Today though, companies must also focus on creating defenses that screen the IT software and service providers who have authorized access into their network.
Threat actors increasingly use supply chain attacks for several reasons:
- Many companies have improved their overall security posture, making it harder for threat actors to find vulnerabilities to exploit.
- Supply chain attacks take longer to detect because they come from trusted third parties.
- The return on investment for ransomware hackers is higher because the compromised vendor can, in turn, infect hundreds of other companies.
How to Strengthen Your Defense
To mitigate the risk of supply chain attacks, we recommend the following steps:
- Log and monitor all third-party access into your network.
- Establish a solid vendor management program so that you know the security practices of every third party you work with, including their incident response plans and cyber insurance policies. You should create a security questionnaire all vendors must complete, and you may want to consider requiring third-party certifications such as SOC 2 for your vendors.
- Implement extended detection and response (XDR) that monitors and correlates data across the network to improve visibility into potential threats on the network.
- Review the security of your own software development life cycle. In another example of a supply chain attack, a recent vulnerability in the Python Package Index (PyPi) left unpatched systems vulnerable to hackers getting write permissions to the pypa/warehouse repository. Hackers could install malicious packages without the developer’s knowledge. The solution: Monitor and regulate software repositories to secure software development and assure continued integrity. We recommend implementing an audit of software dependencies and version-locked dependencies during application auditing. Your organization may not directly maintain these dependencies, but they directly impact your security.
The HBS team can help you create a thorough defense strategy that protects your operations even when threats arrive from your trusted partners. Contact us for a free consultation.






