How to Spot Business Email Compromise
- Written by: Trevor Meers

Ransomware continues to dominate the year’s headlines, but Americans suffer far more damage from business email compromise than any other attack, according to the FBI. The feds reported earlier this year that business email compromise cost more than $2.4 billion in 2021. Throw in business email compromise’s cousin of phishing, and you can tally another $44 million in damages. The boom in business email compromise (BEC) attacks means you should make it a top priority to train your team to spot this scam.
BEC attacks use sophisticated techniques that can trick all but the most attentive email users. Attackers typically impersonate a legitimate contact asking for a transfer of funds. But when victims send the money, it lands in a bank account controlled by the bad guys. The hackers quickly convert the money to crypto currency or shift it into other untraceable channels. It may be days before you even know you sent the money to an imposter.
Hackers typically send an email that seems to be coming from either a co-worker or a legitimate vendor. And, in fact, the bogus message may be coming from a legitimate account that hackers have overtaken. The hacker may even be talking about a legitimate payment you’re expecting to make. The only difference is the account they have you send it to.
The examples below show how BEC attacks work and red flags you can watch for to ensure you don’t fall prey to this ruse.
Stages of Business Email Compromise


Red Flags of Business Email Compromise
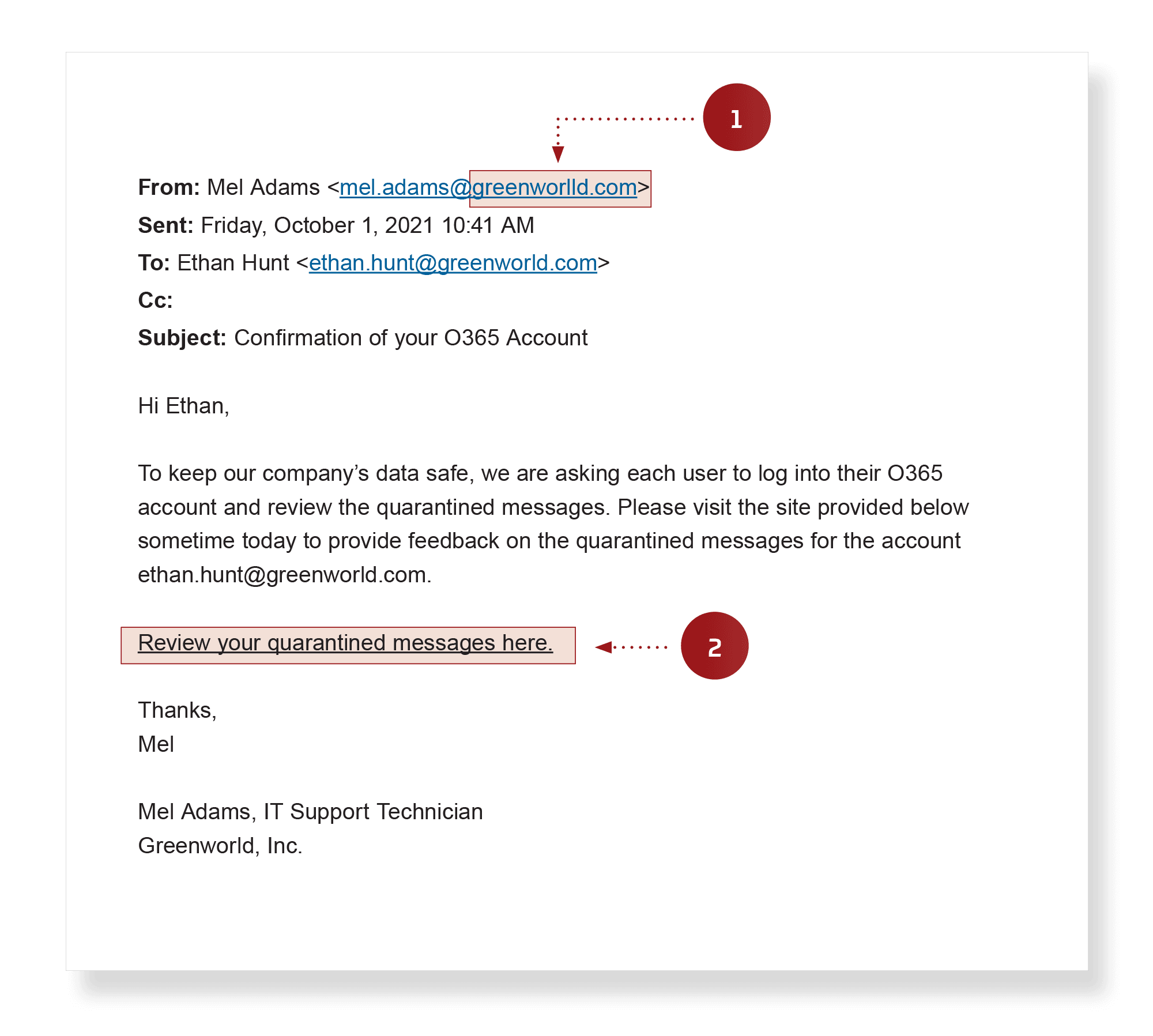
- Spoofed address – Look carefully at the actual domain name, not just the sender’s display name. This spoofed domain has an extra character in the company name.
- Malicious link – This link actually leads to a credential harvesting site. Hover your mouse pointer over the link before clicking it to confirm that it's going to the expected address.
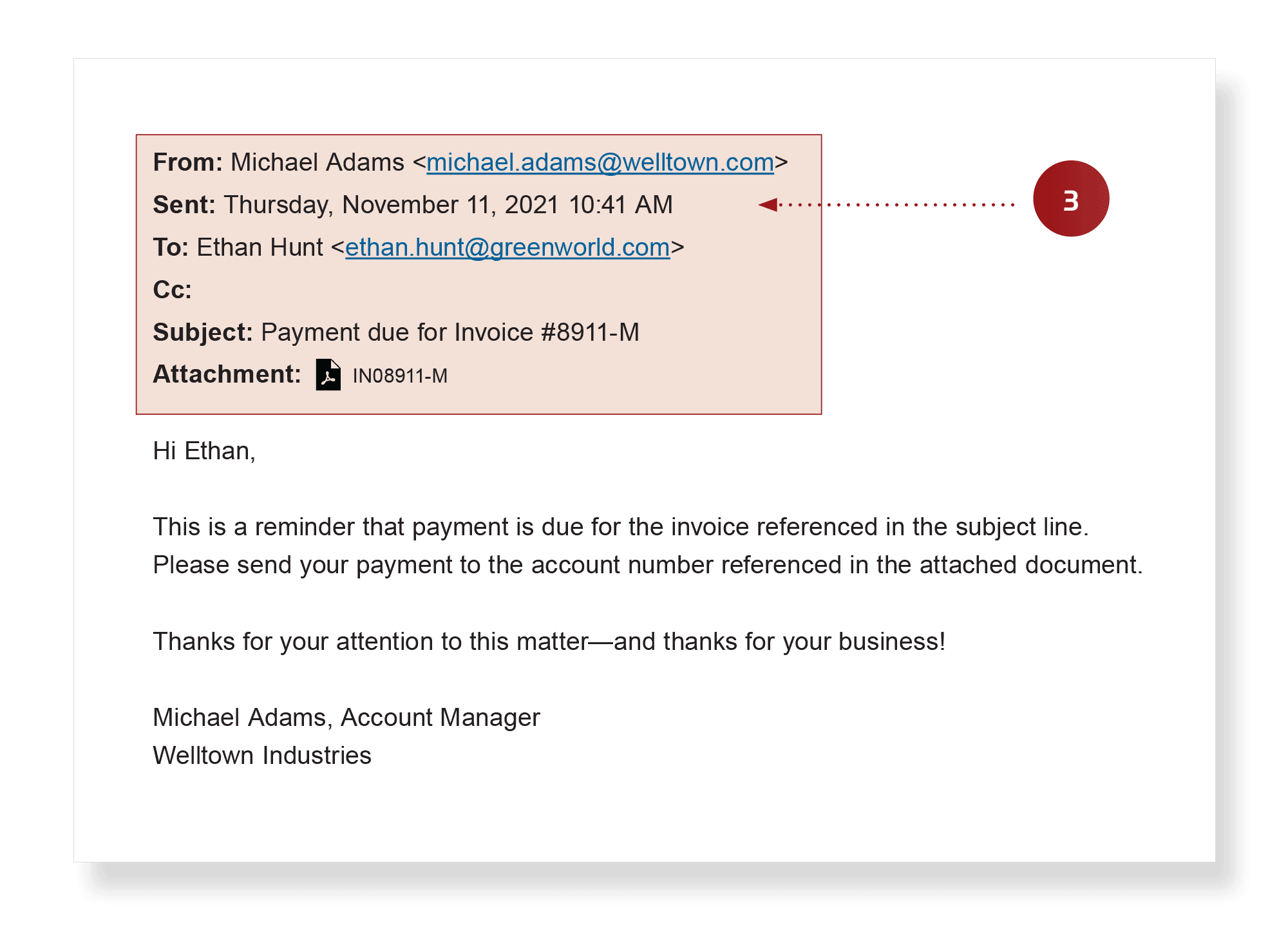
- Real data used to fool you – Because hackers may be monitoring your email, they may jump into a legitimate thread. In this case, the first message in the sequence came from a real vendor talking about a real invoice. The hackers have inserted themselves and took over the discussion, cutting the real vendor out of the thread.
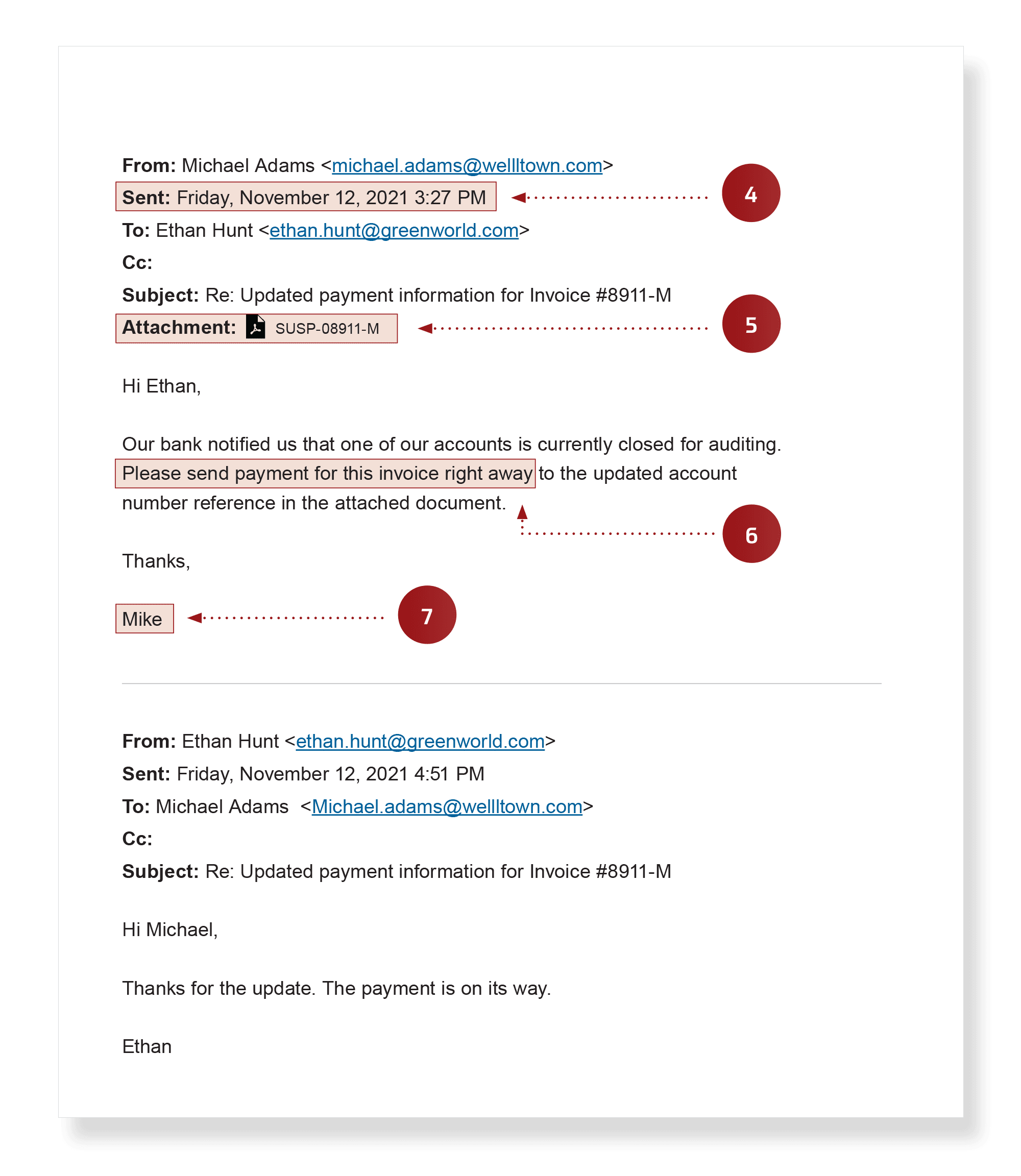
- Timing – This is a fake email from the scammer, who sent the request late in the week, hoping to catch an employee rushing to complete tasks before leaving.
- Suspicious attachments – If you’re not expecting an attachment, don’t open it. Call the sender to confirm it’s a legitimate file.
- Sudden change in normal procedure and/or urgency – Be extremely wary of changes in deadlines, bank accounts, etc. Call your contact to confirm what’s happening.
- Unusual name usage – Hackers posing as legitimate contacts often fumble the details of names, so pay attention to any discrepancies, such as someone who normally goes by “Michael” signing a message as “Mike.”
How to Spot Business Email Compromise
Original message used to steal user credentials:
Spoofed messages used to cause fraudulent payment:
For help with training your team to spot BEC or creating a simulated phishing test for your organization, contact HBS today.






