IAM – Identity and Access Management: Maintaining User Access & Its Importance to Information Security
- Written by: Jim Sixta

Why companies should consider implementing IAM as a part of their defense in-depth strategy
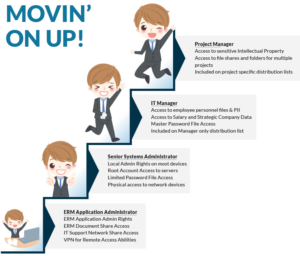
We’ve all seen this scenario. Bob hires on as an ERM System Administrator, performs well and is promoted to Senior IT Administrator. He excels and is promoted to managing 15 IT employees. Eventually he discovers his love for project management and transfers to become a Project Manager. Yes, Bobs are talented individuals!
Often employees move from job to job, department to department, all the while accumulating
access to systems, applications, and data they need to perform their job. But how often do managers remember to remove access from their previous position? Answer ... not as often as they should. Their employees aren't going to complain as they enjoy having their previous access. Little do managers know how much additional risk they adding to the business.
Identity Access Management solutions help enable proper provisioning to reduce the risk associated with an account becoming compromised. Eddy-the-hacker should not be able to access the ERM Application or IT Support Share using Bob’s credentials, if his access had been properly removed during his move up the career ladder. All too often during breach investigations we discover how much access individuals truly have as security consultants comb through the labyrinth of accumulated access. This can easily manifest itself into breach notifications as the number of compromised records and data elements continues to grow. In our example above, Bob would have had administrator level rights to key applications, personally identifiable information for all his employees, and in-depth knowledge of projects within the company.
It surely doesn’t take much imagination to realize the treasure trove of data Eddy-the-hacker just stumbled upon (Darn those Eddys).
Flash forward a couple of years. Bob leaves the company, and his manager hires a worthy replacement, Alice. During the onboarding process his managers submits an IT request for the new employee's access, modeled after Bob's account. Wait, did you catch that? If this were a magic show, you just missed the trick. Now Alice has all the access Bob had, including ERM admin rights, access to personnel files, project file information, etc. Imagine if part of Bob's career path had been in payroll!!!
A proper IAM solution associates one main role to each individual, based on duties associated with their job function. This requires time, analysis of what their employees do, and implementation of Roles associated with those job duties. Managers need to periodically review access their users have, and last but not least, Information Technology (IT) has to collect and correlate data from all the critical applications across the company and present it in way that makes sense to even the most newbie of managers.

Is IAM worth it? The resounding answer is YES. In the long term, your company will:
- Have a clear understand of the security associated with each job function.
- Increase the efficiency AND reduce costs for your security department through faster provisioning with increased accuracy.
- Be better prepared for audits as your roles will already be defined and documented.
- Improve user experience with fewer approvals and one-off provisioning.
Reduce inaccuracies within application security. A fun side effect is during the IAM process, you'll have the opportunity to tune and clean the accounts and roles within each application.






