Why an Information Security Policy, Standards, and Procedures Should Be Top Priority
- Updated: February 6, 2025

Information security policies often fall to the bottom of a company’s to-do list. They aren’t flashy, and writing them isn’t exciting. But these documents are the backbone of a secure and efficient organization.
Investing time in a well-structured information security policy now will better protect your organization from threats, drastically improve compliance, and streamline operations.
What is an Information Security Policy?
An information security policy is a high-level document outlining an organization’s security objectives, expectations, and commitments. It defines how a company protects its data, systems, and networks. But a strong security foundation also includes standards and procedures that turn policy into action.The Three Pillars of Cybersecurity Governance
- Information Security Policies – The "What" An information security policy establishes security goals and priorities. It reflects company values, risk tolerance, and expectations for employees and third-party vendors. It is the vision statement that clearly states your values in this area and what you intend to put into action.
- Information Security Standards – The "How Much/How Often"
Standards support policies by providing detailed expectations. They define:
- Who will implement the standards
- Specific security requirements of associated departments
- Groups affected by the standards
- Compliance with industry frameworks (e.g., ISO 27001, NIST, CIS Controls)
When you’re trying to satisfy most compliance requirements and frameworks, you’ll see and hear a lot about your “policies.” But standards are typically what they’re looking for.
- Information Security Procedures – The “How” Procedures are step-by-step instructions for implementing standards. They ensure that security measures are applied consistently across the organization. For every control area your policy covers, you need to have corresponding procedures explaining how the organization will carry out that policy.Procedures turn policies and standards into tangible action steps. In procedures, organizations should call out specific employee roles and technologies that carry out each procedure.
Why an Information Security Policy Matters
A well-defined information security policy isn’t just there to be there, or to simply check a box—it’s necessary to:- Strengthen Cyber Resilience Policies, standards, and procedures create a clear framework for responding to cyber threats. When a data breach occurs, an organization with a solid incident response plan can react quickly and limit damage.
- Ensure Compliance and Reduce Liability Regulatory requirements like HIPAA, GDPR, CMMC, and PCI-DSS mandate security controls. Cyber insurance providers also assess policies when determining coverage—and how much they charge in premiums. Without proper governance, businesses may face fines, lawsuits, or even denied claims.
- Improve Vendor and Partner Trust Many enterprises require proof of strong cybersecurity before signing contracts. A documented information security policy demonstrates that your organization takes security seriously.
- Reduce Human Error Risks Good security policies equate to employees who understand acceptable technology use, access control, and phishing prevention. By defining security responsibilities, businesses can hold employees accountable while fostering a culture of security.
Real-World Impact of Strong Security Policies
Here’s how having documented policies, standards, and procedures can save your organization.- Data Breach Response: A clearly defined incident response plan ensures teams react quickly, reducing downtime and damage.
- Employee Misuse of Technology: A strong Acceptable Use Policy helps enforce accountability and mitigate risks.
- Vendor Security Audits: Detailed policies prove compliance and protect business relationships.
- Credential Theft: An effective identity and access management (IAM) policy prevents attackers from moving freely within systems.
- Configuration Errors: A change management policy ensures firewall settings and security configurations are properly reviewed.
How to Implement an Effective Information Security Policy
- Identify Security Needs
Every business has unique risks. Identify what policies are required based on company size, industry, and regulatory landscape.
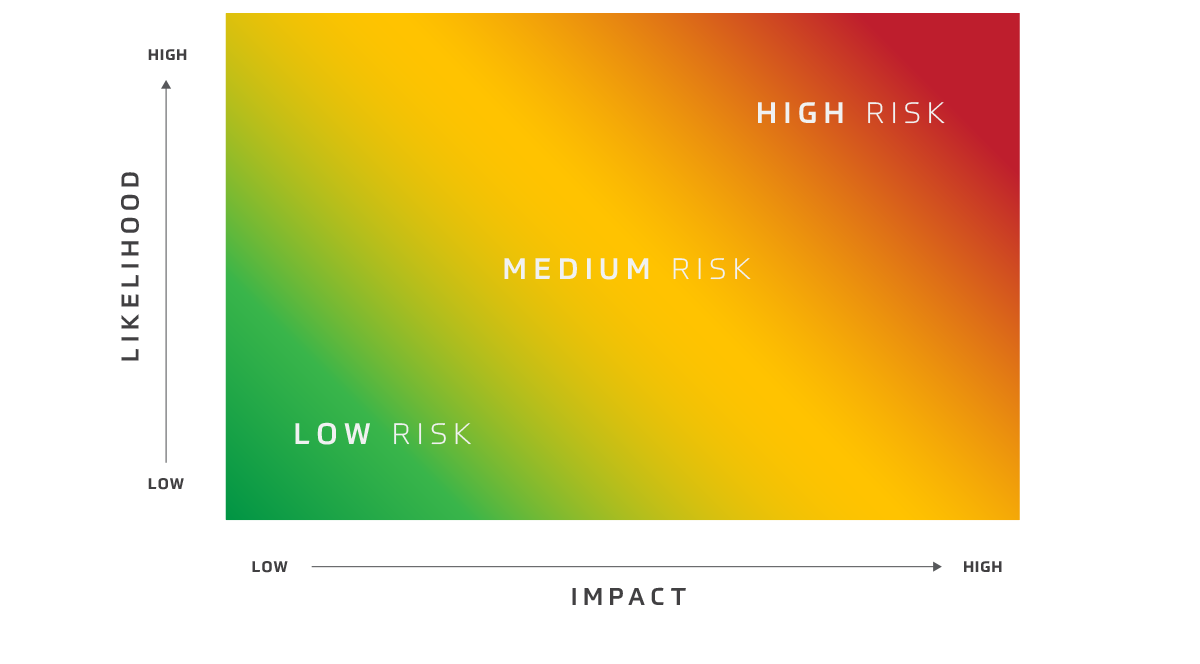
- Develop a Practical Action Plan Work with both IT and security teams to create enforceable policies and make sure they align with business operations.
- Maintain and Update Policies Regularly Security threats evolve. Schedule annual reviews of policies, standards, and procedures to ensure they stay relevant.
- Test and Train Employees Conduct regular training and tabletop exercises to evaluate the effectiveness of security plans. Security policies are only as strong as the people following them.
Additional Resources for Strengthening Security Policies
To help refine and enhance your security governance, consider these resources:
NIST Cybersecurity Framework
CIS Controls
Security Awareness Training
Governance and Compliance
Secure Your Business with Information Security Policies
Writing, implementing, and maintaining security policies doesn’t have to be overwhelming. HBS can help. Our experts assist organizations in developing security policies, ensuring compliance, and building a strong cybersecurity posture.
Need help strengthening your information security policy? Contact HBS today.







 Best practices for securing IT systems.
Best practices for securing IT systems. Employee training to reduce security risks.
Employee training to reduce security risks. Expert assistance in building and maintaining security policies.
Expert assistance in building and maintaining security policies.