What Are Fileless Malware Attacks?
- Written by: Trevor Meers
Every ransomware update you’ll hear right now includes discussion of a growing threat that goes by multiple names. Fileless malware. Living-off-the-land attacks. Memory-based attacks. Non-malware attacks.
Whatever you call it, the fileless malware threat is growing and extremely evasive—but you can mount a meaningful defense. In this blog, we talk with Senior Penetration Tester Jason Moulder about the growing issue of fileless malware attacks, how they work and how you can create an effective defense against this slippery enemy.
Fileless Malware Basics
Fileless malware attacks give almost no sign of entry and leave almost no evidence in their wake. If a data breach were a physical burglary, a fileless malware attack would look something like arriving at your office to find the company’s secret formula missing from the vault. Yet there’s no sign of a broken lock, overturned furniture or even a footprint in the carpet. The bad guys seem to have materialized in the vault and evaporated with the goods just as mysteriously. The reality, however, is that they somehow convinced one of your trusted employees to steal the formula using their approved access to the vault.
In the same way, fileless malware attacks without introducing a foreign file into your system. It sneaks into legitimate operating system processes (especially Windows PowerShell) and works against you. That makes it extremely hard to detect through traditional antivirus software, which works by looking for known file signatures.
This hacking technique has been surging lately, as fileless malware attacks jumped 900% in 2020, according to one report. One study found that 74% of malware attacks in Q1 2021 were zero-day attacks, which includes any attack that doesn’t shown up in the databases of signature-scanning tools.
How Fileless Malware Works
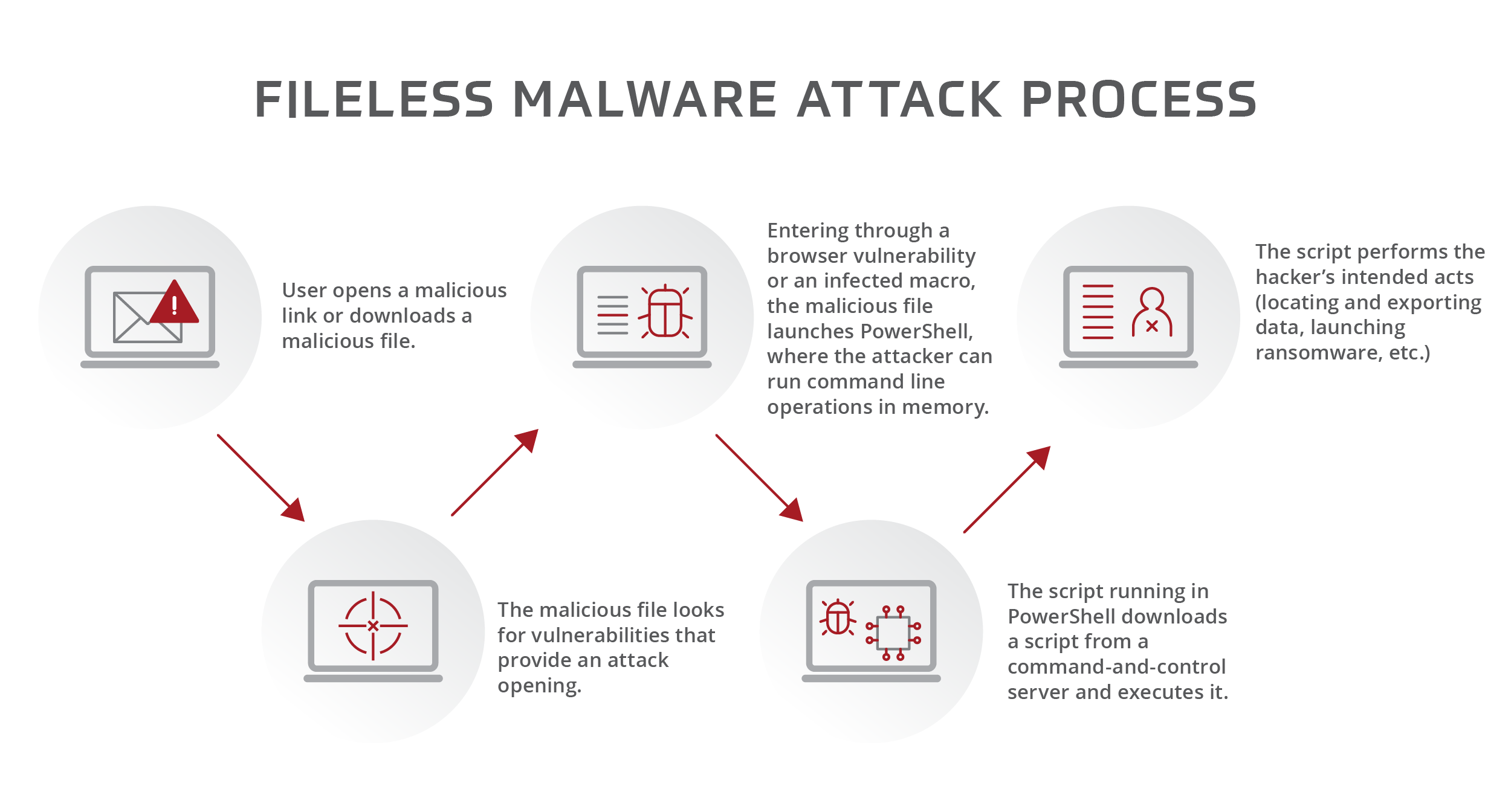
Because these attacks leverage scripts within your legitimate software to launch their attacks, they’re a bit like a digital cancer, with hackers turning the system’s own elements against it. With no file installation to detect, antivirus programs usually can’t see them. And because the fileless malware exploits trusted applications or the operating system itself, whitelisting apps you consider dangerous won’t do any good. The most common vectors in fileless attacks are scripts that exploit Windows’ PowerShell, accounting for up to 90% of fileless attacks in some studies. Hackers also frequently leverage Windows Remote Management (WinRM) in fileless attacks.
Senior Penetration Tester Jason Moulder, who spends his days getting inside hackers’ minds, calls fileless malware one of the most elusive threats in play. “If you were to scan all the communication between all the APIs in your system every day, you’re looking at an incredible amount of data. If you look at your Task Manager, you’ll see certain elements running 50 times simultaneously because it’s used by multiple programs. That’s what makes fileless malware such a great attack avenue. The malicious activity gets lost inside the normal activities that make your operating system function.”
Digital forensics investigations struggle to analyze how attacks happened because the malicious script runs in memory and disappears after the system restarts.
Hackers also like this form of attack because it gives them admin access to an endpoint, letting them exploit it as a gateway to the rest of the network.
Common Fileless Malware Carriers
The security community has identified scores of binaries, scripts and libraries that hackers use in fileless attacks. (You can browse a list here.) Here are some of the most common ways that hackers get a foot in the door for these attacks:
Web scripts – Hackers often launch malicious scripts through JavaScript, a staple of web page design. (Hackers also relied on the popular Flash web-based script before it was officially discontinued early in 2021.) Hackers lure users into clicking a link in an e-mail that takes them to a website that looks legit but is set up to scan for vulnerabilities and slip malicious code into the system. That means, as usual, that social engineering is a critical vulnerability you need to shut down through better user training.
PDFs – The issue with this ubiquitous file type typically revolves around opening PDFs in the web browser by default, which triggers one of the scripts hackers seek to exploit by blending their code into legitimate processes. “For example,” Jason says, “you can write something for PowerShell that says, ‘When you open this, open this command in the background and go get this file from the Internet.’ Whenever it goes to this website, that site can load something into memory.”
Microsoft Office macros – Similarly, Office macros run scripts that give hackers a chance to piggyback with their own malicious scripts. In response, Office now automatically blocks most macros. But Jason warns, “You can still trick people into enabling the macro. It may require some limited user action to initiate it, especially if it’s a Word doc or a PDF. When they click it to open it, that part is written to disk and can be seen in forensics. But once it’s loaded into memory, that’s where it can get lost pretty quickly.”
How You Can Protect Yourself
Security leaders engage in a daily arms race with hackers as each side counters new moves by the other. While fileless malware presents a serious threat, you can actively defend against it with the following steps.
Implement managed XDR – A managed XDR service like HBS’s provides complete monitoring across your entire system through SIEM, endpoint detection and response and 24/7 SOC analysts interpreting the alerts that come in. Managed XDR spots suspicious activity and correlates signals to form a picture of a developing threat, even when it’s caused by something other than a known malicious file.
Jason points to the following indicators that XDR can pick up as the sign of a brewing fileless malware attack:
- Numerous queries against Active Directory related to user and domain enumeration. That could give away an attacker preparing to pivot by exploring what access they have.
- Legitimate activities chained together in unusual ways. “If someone initialized a connection and then tried to impersonate an administrator or grab a Kerberos ticket, that’s not something that should happen,” Jason says.
- Suspicious password activities. If your monitoring solution sees NTLM hashes being passed instead of legit passwords, that could be suspicious. It may mean someone scraped that from memory and doesn’t know the legit passwords.
- Multiple admin logins from the same person or logins outside of normal hours.
- Unapproved versions. If you prefer a particular version of PsExec, for example, whitelist only that version in your system. That makes it easier to spot someone running a different hashed version.
Limit user access – Many fileless malware attacks target users with wide-ranging network access, using compromised credentials to pivot throughout the system. By limiting users to only the data they really need (as described here), you can limit hackers’ ability to move laterally if they get in.
Jason calls specific attention to admin accounts. “Using the default admin built into Windows is a very bad habit because once you have that account, you can go pretty much anywhere,” he says.
Train employees – This advice never goes out of style. Teaching employees to recognize and avoid suspicious links will greatly reduce your risk by preventing malicious scripts from ever getting the chance to scan a device and go to work.
For advice about you can protect your specific system from the ever-changing fileless malware threat, contact HBS today.






